If you use the vulnerability that exists in the fax communication standard "T.30" set by the iTu-T, you can cause a buffer overflow just by knowing the target fax number and take over a digital multifunction machine (MFP).。Furthermore, if you combine the vulnerability attack tools used in the ransomware "Wannacry", it will be possible to increase the invasion of PCs and servers in the office network with a multifunction device, and steal confidential data.――.
On August 12, 2018, at the hacker event "DEF CON 26" held in Las Vegas in the United States, the lecture "What the Fax!?" That introduces these attack methods (lecture title is Net Slang "WTF = What."THE FUCK "is also.Janef Barmas and Ayal Itkin, a security researcher of CHECK POINT Software Technologies, who gave a lecture, stressed that the attack method was effective in many multifunction devices and manufacturers and users should respond immediately.
Image of attack procedure.The attack file is sent to fax, hijacking a multifunction device, and it can also invade into the internal network (image is from CHECK POINT blog).
"Pipipit ... Pee -oh, holororororo ...
At the beginning of the lecture, Balmas, who invites the laughter of the venue to play the "example sound" at the time of faxing, has evolved into a digital complex that integrates the functions of copier / printer / scanners.Explains that there are various connection interfaces such as Ethernet (LAN connection), USB, and Bluetooth, as well as telephone lines.
Janif Balmas, a security researcher of CHECK POINT SOFTWARE TECHNOLOGIES
However, there are many ways to communicate with faxes in all aspects, such as emails.The Internet generation and mobile generation tend to think that "I don't use faxes nowadays", but when Balmas actually searched Google, the "over 300 million" fax number was hit.The exchange of faxes is rooted as a custom, and there are many industries and regions that have not been switched to other means.The representative is Japan.
"For example, in the world of ships, naigatures are exchanged by faxes, and some banks and administrative organizations are limited to mail or faxes. In Japan, it is more surprising. In Japan., It seems that more than 90 % of companies still use faxes as active. "(Barmas)
When Japan was named, I looked into it and found a statistical material from the Ministry of Internal Affairs and Communications, "2006 (2006) Communication Usage Survey".According to the report, the FAX holding rate in domestic establishments is "97.8 %".It was more than 10 years ago, and I would like to believe that it is not so high now, but the other day, I just experienced "only faxes" in a service procedure.He was able to send a fax from a high -performance multifunction device at a convenience store, but was this an advanced life?
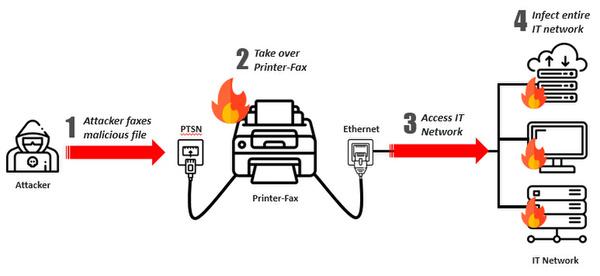
Aside from that, there are still many companies and industries that use faxes for various exchanges.And in the current office, many faxes are functionally integrated into digital multifunction devices, leading to an internal network at the same time as the FAX line."Then, maybe there is a possibility that you can enter the internal network via a Fax line."Balmas and Itokin, who thought so, started a survey immediately.
I would like to start by investigating the structure of the multifunction device and exploring the possibility of attack.Balmas and Itokin chose HP Inc.'s business complex "OfficeJet Pro" as a survey.The reason was that the price was cheap and easy to obtain, but also the HP was a major company with about 40 % share in the US printer market.
HP business multifunction device that was surveyed.As described later, it is important to note that the effects of the vulnerabilities discovered this time extends not only on the website but also on the multifunction devices of all manufacturers.
They quickly dismantled the obtained complex and checked the board.On the board, there are ports printed on the substrate that are printed with "JTAG (port for debugging CPUs and substrates)" or "Serial Debug (general -purpose port that outputs kernels and application logs)".When I tried to connect to this port, JTAG was disabled, but the Serial Debug interface seems to be alive.
They are considering how to invade with the firmware as a foothold, and thought that if they were able to debug, they would know how data would be handled by firmware.I want to use the Serial Debug port somehow, but even if I connect it to a serial connection here and hit the command such as "DIR" or "READ", I only returned the response "error: I don't undertand".Apparently, some functional restrictions are applied.
Demanded multifunction device board.There are ports such as "JTAG" and "Serial Debug"
As a result of repeated surveys, the security vendor Senrio in July 2017 has an old version of the XML library "Genivia GSOAP" (Ver.2.7-2.8.47), and the SOAP_GET function has a vulnerability of stack overflow.Was announced.At the same time, Exploit "Devil's Ivy" has also been released (CVE-2017-9765).
This vulnerabilities also exist in the OfficeJet Pro, which is the subject of this survey, and if you use Devil's IVY to send 2GB or more XML files via TCP/53048 ports, a buffer overflow will occur and promoted authority (capture system authority.) I realized that I could aim.
By the way, the firmware was obtained from the HP download site."The firmware of all products sold by HP was posted. Anyway, it took two weeks just to look for the target firmware," said Barmas.
After the analysis environment was in place, they began to investigate the internal configuration in earnest.The OfficeJet Pro to use the ThreadX -based real -time OS, the main CPU is a 32 -bit ARM processor, and is shared for communication between the CPU and the MCU (micro controller unit) that controls the LCD screen.It turned out that it supports the transmission and receiving color fax based on the T.30 protocol.
The compounding element of the surveyed multifunction device, OfficeJet Pro, is found!
The T.30 is one of the fax communication standards set by iTu-T.The first edition (version) was released in 1976, and in 1995, a color fax expansion standard was added in 1995.The T.30 last updated in 2007.
In this survey process, an important fact was found on the color fax communication specified in this T.30.In the color fax, JPEG data is sent and received, but the receiving terminal saves the JPEG data as a JPEG file without sanitizing (insufficient treatment).If it contains a JPEG marker (one of the labels of the data structure) that is not supported by the receiving side, the part should be implemented to destroy and skip the reception, but that is the case.do not have.
There is a gap for the attacker here.If you know the fax number to be attacked, you can store the file in a target multifunction machine by simply creating a JPEG data with an illegal code and sending a fax.This is a great opportunity for the attacker.