Microsoft confirmed on March 22 that there was "limited access" to one account in an attack that appeared to involve the hacker group "LAPSUS $". The company's security team says it stopped the attack prematurely.
LAPSUS $ said on the 21st that it hacked Microsoft and revealed that it got a part of the source code of "Bing" "Bing Maps" "Cortana". Microsoft's research team said it had been tracking LAPSUS $ as "DEV-0537" for several weeks. LAPSUS $ targets government agencies, high tech, telecommunications, media, retail and medical industries around the world. A group of South American hackers are believed to have been involved in data leaks from Samsung and NVIDIA.
According to a blog post published by the Microsoft Threat Intelligence Center (MSTIC) on the 22nd, "DEV-0537 is known for using a pure threat and destruction model without deploying the ransomware payload. ". "DEV-0537 is also known to hijack individual user accounts on cryptocurrency exchanges and leak their cryptocurrencies" (MSTIC).
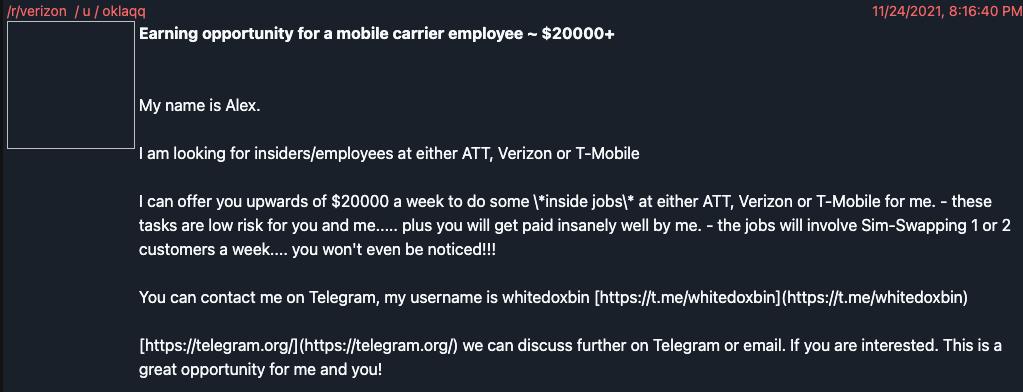
The group uses means such as phone-based social engineering, SIM swapping, and paying employees and vendors of targeted organizations to obtain credentials, Microsoft said. LAPSUS $ doesn't seem to be trying to hide its activity. It advertises its intention to purchase credentials and announces attacks on social media.
"When the attacker announced the intrusion, our team was investigating the accounts that had already been compromised based on threat intelligence," Microsoft said. , Our team was able to block the activities of the actors along the way and limit the spread of the impact. "
The number of data breaches is increasing in every industry. According to a report from the Identity Theft Resource Center, the number of data breaches in 2021 in the United States increased by 68% year-on-year, a record high.
LAPSUS $ also claimed to have committed an unauthorized access attempt in January targeting Okta, an identity management and authentication service. Okta CEO Todd McKinnon said yesterday that the January issue was "contained" and that there is no evidence of continued malicious activity since then.
This article was edited by Asahi Interactive for Japan from an article from overseas Red Ventures.