In July, ransomware infected a domain controller, the county's network services went down, and email became unusable. Since there is no hope of recovery even after three weeks, the city council resolved to pay a ransom worth 130,000 dollars (about 14 million yen) with Bitcoin, and by actually paying the criminal side for decryption Get the key to recover
In both of these cases, city officials unfolded the document attached to the email, which led to a macro being executed and infected with ransomware, causing damage to the organization at once. Both infected malware is said to be "Ryuk", which is a ransomware for targeted attacks, and in the case of Lake City, Emotet and Trickbot infections have been further confirmed.
Macro execution of Word documents attached to emails is likely to trigger Emotet infection.It is desirable to select "Display warning and disable all macros" in the macro settings.There are several attack patterns behind the large-scale damage caused by ransomware. Especially striking is the pattern of using Emotet as a “carryer”.
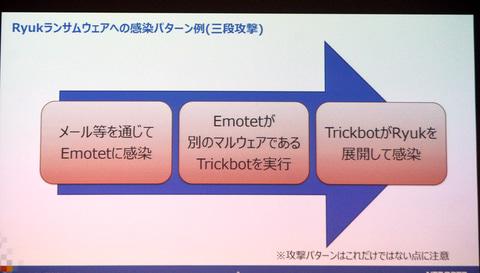
The attacker first spreads the attachment file containing the malware to the target through e-mail etc. and infects the PC with Emotet. Emotet collects the sender's name / email address, destination name / email address, and the subject and body of the sent email from the email software (Outlook) of the infected PC using its own email collection mechanism. Based on this information, a reply-type email is sent to the parties concerned in the form of hanging (entering the thread) in an arbitrary subject.
It is difficult for general users to tell whether the reply email that arrives at the thread starting with "Re: xxxx" is due to malware. By inducing these misidentifications, Emotet increases the number of infected PCs and does more damage-the first groundbreaking to bring greater benefits to attackers.
Emotet sneaks into the target PC or system and then downloads another malware, "Trickbot." Trickbot, a modular malware, adds various functions (login ID, password, collection of browser data, etc., interface invalidation, connection with C & C server, domain controller detection, etc.) as modules from its structure. Is possible and be prepared to maximize its effectiveness before installing the ransomware.
Based on the information stolen by Trickbot, the attacker invades the core target of the system such as the domain controller, executes Ryuk's payload, starts encrypting the file on the infected PC, and spreads on the network. , The pattern is to spread the infection of ransomware.
Emotet is a very good malware as the first trigger to succeed in these multi-stage attack patterns.
An example of a ransomware attack pattern originating from Emotet All files are encrypted on a PC hijacked by the ransomware Ryuk, making it completely inaccessible.